The following guide is to help the deployment of an Azure OpenID configuration as the authentication provider for Pyramid. Azure is not that different to generic OpenID, but there are some key aspects that are unique.
Note: This feature is only available with Enterprise licensing.
Azure OpenID Setup
Setup new App Registration
Log in to the Azure portal, navigate to 'App Registrations', and create a new registration.
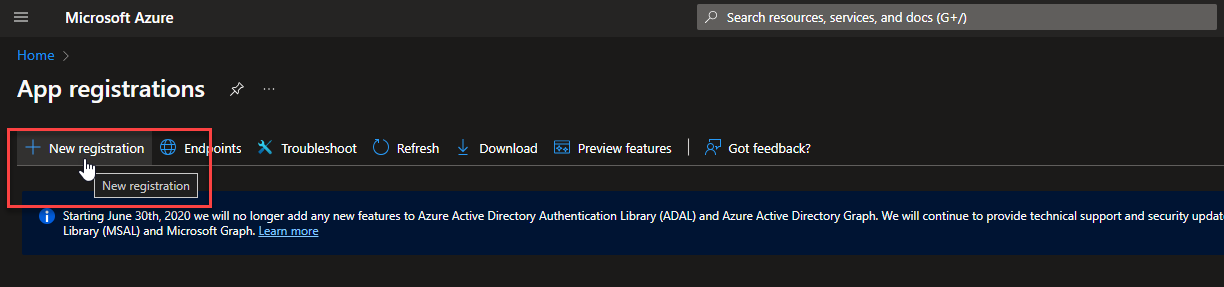
Name the application and set the redirect URI To Web and set the value to https://<my-pyramidsite>.pyramidanalytics.com/login/openid_callback
Click Register.
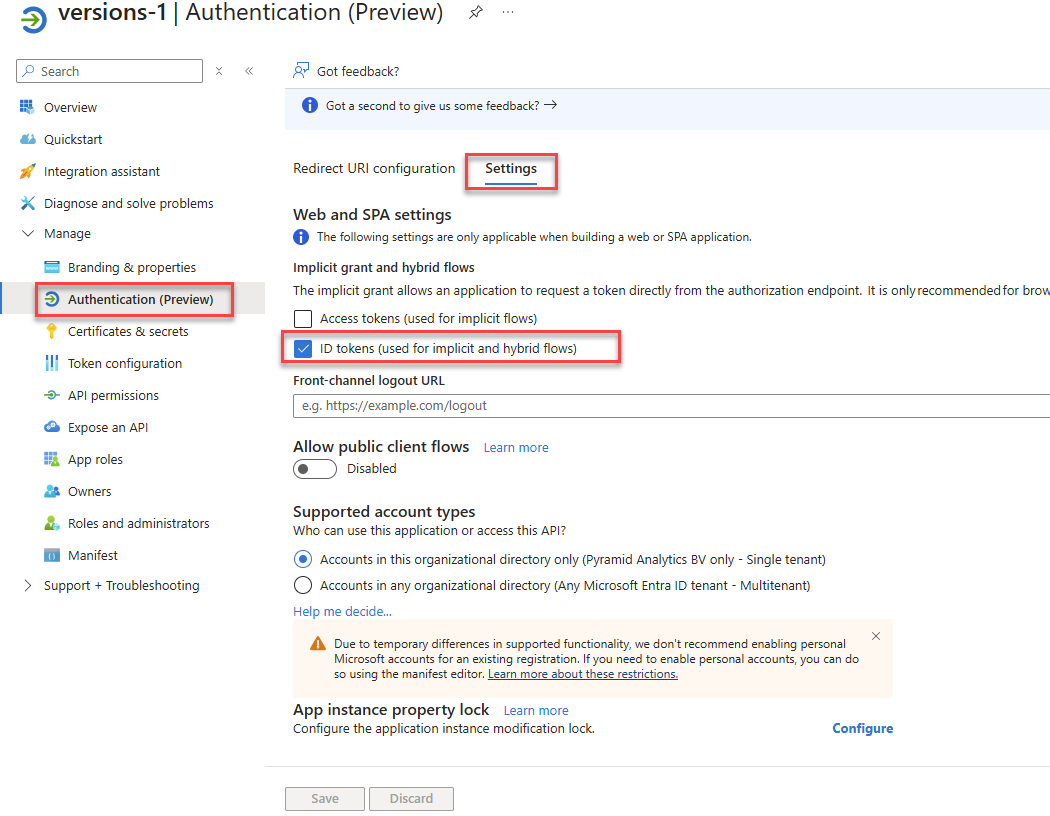
Enable ID Tokens
Inside the application, you need to enable ID tokens as shown below:
Setting the provider up in Pyramid
- In the Admin Console, click Security > Authentication.
- From the top-right of the page, click Change Provider.
The Authentication Provider page opens with the details of your current Authentication Provider displayed.
The Change Provider page opens. You will copy the details of your new authentication provider into this page, starting by selecting your Provider.
Take all the setup information from the previous steps to fill in this form:
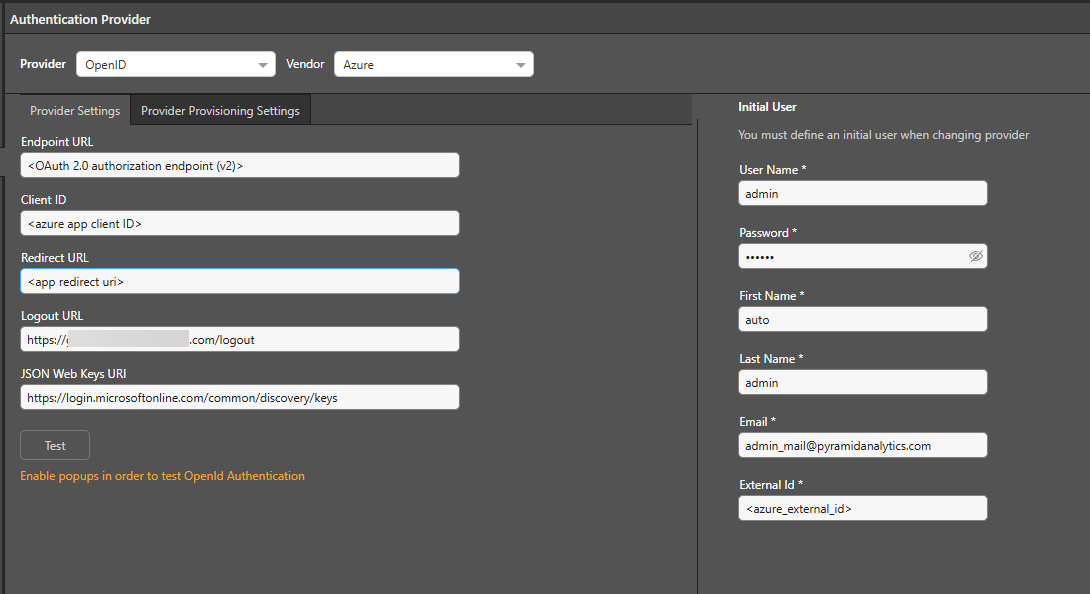
- Endpoint URL: Authorization URL
- Client ID: Client ID
- Redirect URL: Redirect URI
- Logout URL: The URL address that will be used when the user logs out of the Pyramid app
- JSON Web Keys URI: https://login.microsoftonline.com/common/discovery/keys
Test the setup and Initial User
Click Test to test the connection. If the test works, you will see this pop-up:
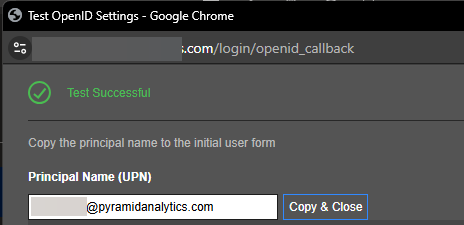
Copy the Principal Name (UPN) and paste it into the External ID field in the Initial User details.
User Provisioning Setup
The Azure OpenID provider can be used for auto provisioning in Pyramid. If you want to use auto provisioning, you will need to set up the app and then specify its settings on the Provider Provisioning tab. For more information, see Azure User Provisioning.
Save your changes
Click Apply to start the provider change-over process. At this stage, the existing users (attached to the previous authentication system) need to be converted over.
Admins will be prompted to either:
- Delete all existing users and their local content. When users are deleted by this process, all their private data (the discoveries, publications, and so on that are stored in their My Content Folder) is "soft deleted." Soft deleted files are moved into the Deleted users content folder and can be restored by an admin if needed.
- Convert old users to the new provider (through the user conversion wizard), and keep their content
Since this exercise cannot be rolled back once the changes are committed, admins need to step through this exercise carefully.
- Click here for a detailed explanation and walkthrough of User Conversion